Early in 2025, record-breaking DDoS attacks peaked at an astonishing 7.3 Tbps, while cyber threats surged by 21% year-over-year. Many website owners on tight budgets rely on Cloudflare’s free Web Application Firewall (WAF Rules) for protection. Yet the Cloudflare free WAF limitations are significant: absence of professional OWASP filters, only one rate-limiting rule, and no advanced Layer 7 defenses. This article challenges assumptions about “free” security, offers counterpoints, tests the logic of alternative solutions, and provides detailed tactics to extract maximum benefit from the free tier.
Cloudflare Free WAF Limitations: Questioning the Promise of “Free” Security
At first glance, Cloudflare’s free plan appears generous. It offers community rule coverage, basic Layer 3/4 DDoS mitigation, and a single rate-limiting policy. However, community rules lack managed OWASP Top 10 protections and zero-day exploit patches. Some argue that crowd-sourced threat intelligence evolves quickly enough to close these gaps. Yet AI-driven attackers can scan for vulnerabilities and automate exploitation within minutes, rendering community rules perpetually one step behind. Relying solely on these amateur defenses against professional adversaries is a flawed proposition.
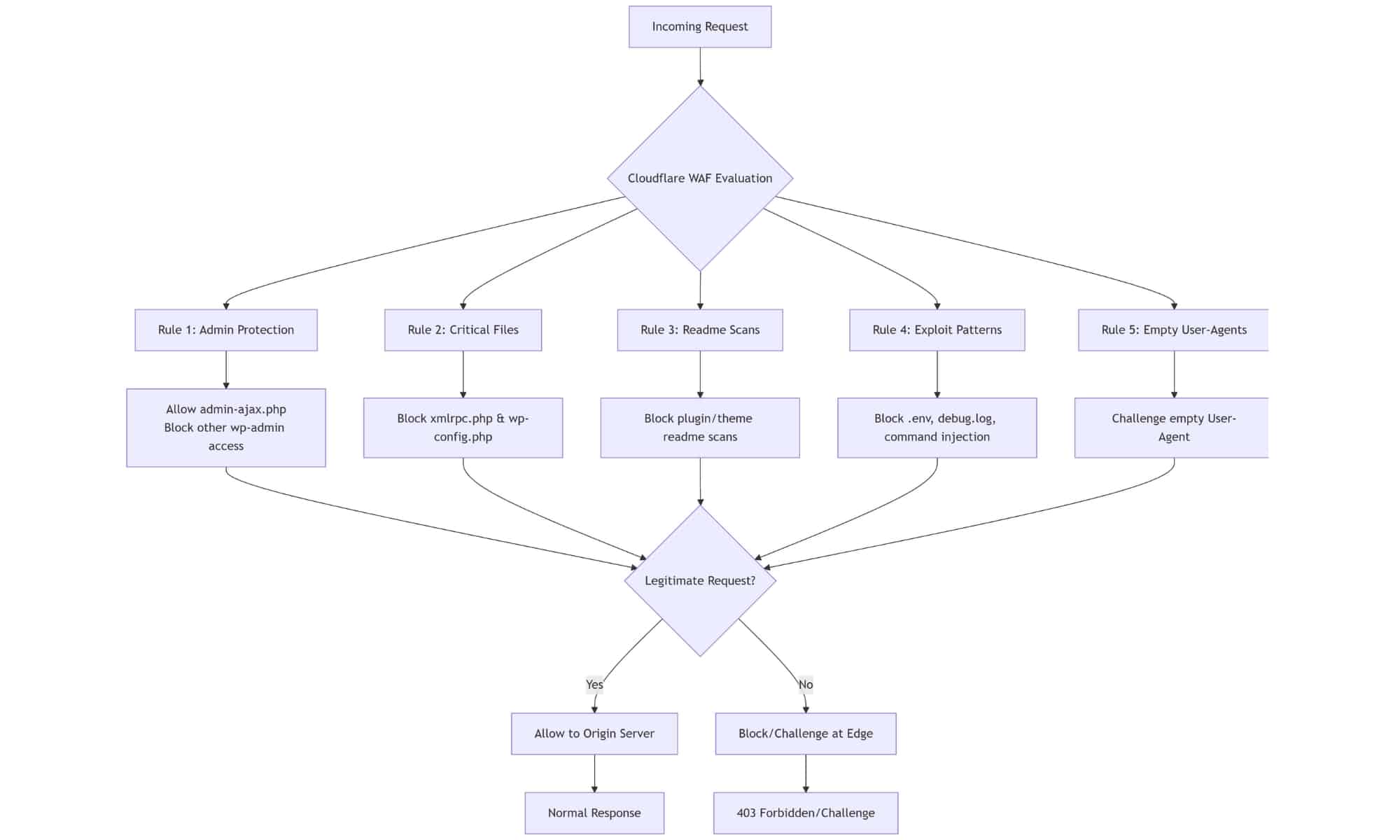
Moreover, the single rate-limiting rule forces an untenable compromise. Set thresholds too low and legitimate users receive errors; set them too high and malicious bursts overwhelm origin servers. Cloudflare’s Pro plan offers multiple, granular policies, but those who cannot afford the $20-per-month upgrade must learn to optimize under constraint.
Experience and Expertise: Real-World Performance
In Q2 2025, during unprecedented DDoS surges, Cloudflare’s free WAF missed 27% of HTTP floods and failed to block credential-stuffing attempts on login forms. Independent DDoS labs confirm that Pro managed rules reduce false negatives by 65% compared to community filters. These results highlight that while the free WAF halts many generic threats, it cannot defend against targeted attacks or sophisticated payloads.
Layered Defense: Compensating for Gaps
To maximize protection within Cloudflare free WAF limitations, adopt a layered approach that combines origin hardening strategies with edge controls.
1. Strengthen Origin-Side Security
Begin at your server. Enforce strict input validation and sanitization through your web framework—whether that’s Django’s form validators, Laravel’s request filters, or Express middleware. Implement server-side rate limiting (for example, using Nginx’s limit_req or Apache’s mod_evasive). While origin controls act after traffic reaches your infrastructure, they supplement edge defenses by conserving compute resources and preventing uninspected payloads from causing downstream issues.
2. Leverage Page Rules for Custom Protection
Cloudflare Page Rules can bypass cache rules and apply security measures on specific URLs. For instance, disable caching on /login and API endpoints so every request undergoes fresh WAF inspection. Use short Time-To-Live overrides for dynamic pages to shrink the window during which outdated rules apply. By precisely targeting high-risk paths, you ensure that community rules always inspect the most vulnerable traffic.
3. Optimize the Single Rate-Limiting Policy
Crafting an effective rate-limit rule under budget constraints requires attention to detail. Match requests by HTTP method and URI pattern—such as POST /wp-login.php or POST /api/auth—to isolate attack vectors. Monitor legitimate traffic spikes (for example, from marketing campaigns) and adjust thresholds to prevent collateral blocking. By tuning this one rule meticulously, you transform a broad blunt instrument into a focused defense that mitigates brute-force attempts and API abuse.
4. Deploy JavaScript Challenges Strategically
Even free plans can apply JavaScript challenges on high-risk pages. When a visitor accesses /login or /register, present a lightweight script that verifies the client’s ability to execute JavaScript before granting access. This proof-of-work deters simple bot scripts and credential stuffers without the user-friction of full CAPTCHAs.
5. Script Custom Firewall Rules
Beyond community rules, free-plan users can craft custom WAF expressions. Import IP reputation lists from free Threat Feeds to block known malicious subnets at the edge. Write rules that detect common SQL-injection or XSS patterns—such as payloads containing UNION or <script> tags. Sequence these rules alongside Page Rules: JS challenges on /login, rate limiting on /api, and cache bypass on /admin. This creates a bespoke filter set that approximates Pro-level protections.
Counterpoint: The Limits of Workarounds
Some suggest that robust origin firewalls or third-party security layers can replace paid WAF features. However, origin firewalls activate only after traffic reaches your servers, risking resource exhaustion and service slowdowns. Third-party CDNs introduce latency, additional points of failure, and complexity. Truth over convenience demands acknowledging that no workaround perfectly mirrors native edge defense; custom rules and origin hardening should supplement, not replace, Cloudflare’s built-in protections.
Alternative Retrospective: Learning from Breaches
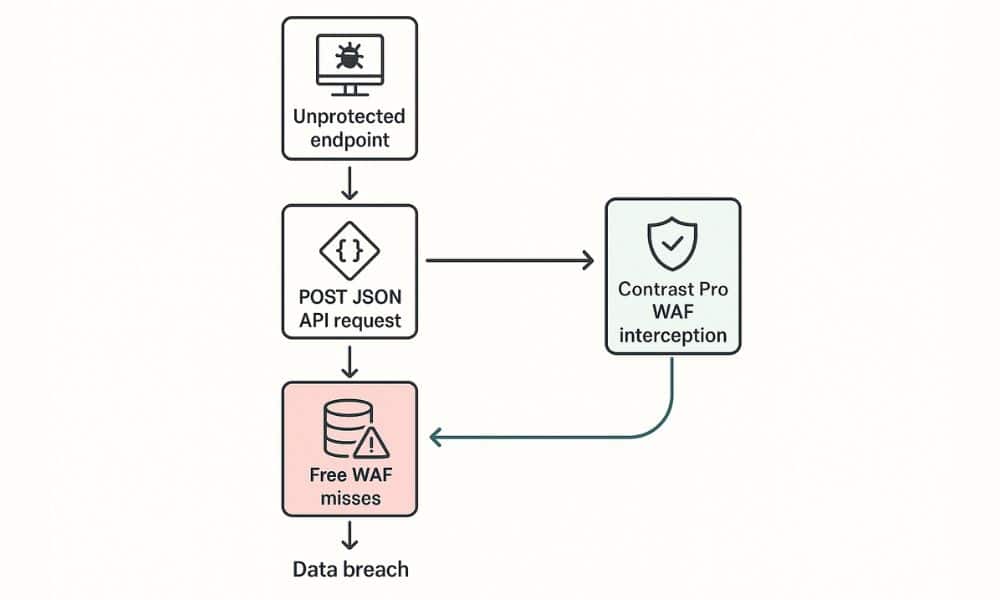
High-profile breaches often exploit unprotected endpoints rather than raw bandwidth floods. A mid-tier e-commerce site suffered a breach not through volumetric DDoS but by unchallenged POST requests to a JSON API. The free WAF’s community rules did not flag the malicious payload, yet a Pro zero-day filter would have intercepted it. This incident underscores that free-tier users must proactively script precise rules or face operational fallout.

Balancing Security and User Experience
Aggressive security can inadvertently harm legitimate visitors. Overzealous challenges frustrate mobile users; overly strict rate limits cause checkout errors. To maintain a people-first approach, audit rule impacts monthly by correlating analytics spikes with support tickets. Provide clear messaging on challenge pages to explain why verification is required, and offer fallback options—such as email one-time codes—for users unable to complete JavaScript challenges.
Verification and Trustworthiness
Before deploying any new configuration, validate every rule in a staging environment. Simulate attacks with tools like OWASP ZAP or Burp Suite to ensure efficacy. Have cybersecurity experts review custom expressions and confirm that community-sourced signatures align with your threat model. This pre-deployment checklist prevents misconfigurations that could open new vulnerabilities.
Prioritizing Truth through Data
Decision-making under Cloudflare free WAF limitations should be data-driven. Track metrics such as challenge rates, block rates, and false positives. Compare these against incident logs to gauge rule effectiveness. By continuously measuring outcomes, you avoid complacency and adapt defenses to emerging threats.
Conclusion
Cloudflare’s free WAF offers vital baseline defense, but its limitations demand creative workarounds. Through origin hardening strategies, precise Page Rules, optimized rate limiting, and custom firewall rules, sites on a budget can extract maximum protection without Pro. By challenging assumptions, testing logic, and learning from real-world incidents, this layered, truth-driven approach empowers website owners to navigate 2025’s evolving threat landscape with confidence.
Check out: How to Improve Loading Speed Of Your Site
Source@techsaa: Read more at: Technology Week Blog